In this issue:
- The Hack: When Crime Pays Fractions of a Penny on the Dollar
- Jio!
- The Bans: Huawei Employees. Party Members? Dollars?
- Slacktivism
- Slackifying
- Micro PE
- Airbnb
The Hack: When Crime Pays Fractions of a Penny on the Dollar
Stories about finance and spying sometimes have very different details but the same basic plot. They both revolve around information asymmetries, and at the highest level they’re both about judiciously using an information edge without revealing it. When the NSA decides whether or not to act on information, when it would reveal how they got the information, they’re behaving the same way a fund manager does when he patiently accumulates a stock over the course of weeks instead of buying a big chunk all at once. And a well-executed intelligence operation has the same inside-the-OODA-loop look as a good trade: a series of events that look like unfortunate coincidences for one side and very lucky ones for the other side suddenly snap into focus as it becomes apparent that one group knew something the other group didn’t. (There are practical barriers to figuring out something you don’t know, but there are high psychological barriers to realizing that someone else knows something about you that they shouldn’t know.)
There’s not a lot of overlap between the two fields, at least in equities, because much of what spies do qualifies as gathering material nonpublic information. So it’s mostly a fun side interest. One person who understands the deep connection between bean-counters and spooks is Neal Stephenson, whose Cryptonomicon is all about money, information, and signals intelligence.
One question that comes up a lot in Cryptonomicon is: when is something that’s normally an asset actually a liability? At several points in the book, characters end up with assets—stock in a valuable but vulnerable company, particular GPS coordinates, an understanding of what other characters are up to—that makes them much worse off, even if their implicit balance sheet looks better.
This came to mind during yesterday’s twitter hack.
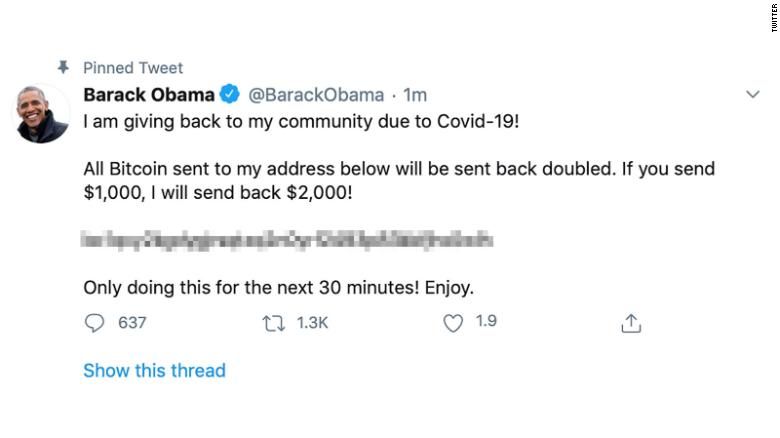
The hack, in case you missed it: several Twitter accounts posted links to Bitcoin-related scams, either soliciting Bitcoin donations for fake charities or promising to double people’s money if they sent Bitcoin to a specific address.
Here’s Obama:
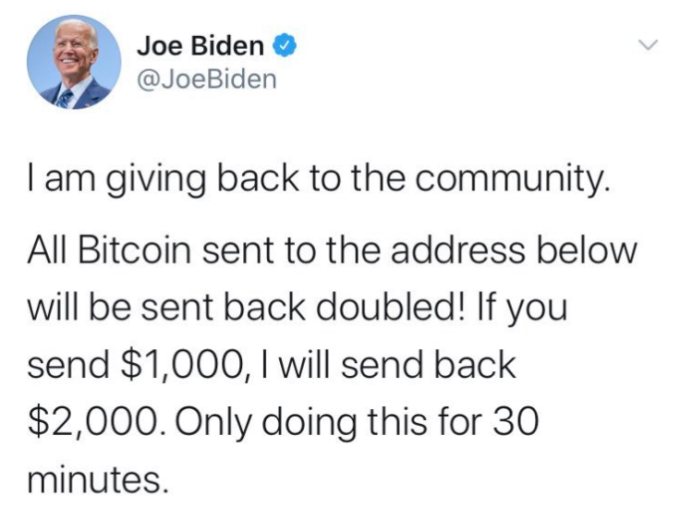
Here’s Joe Biden:
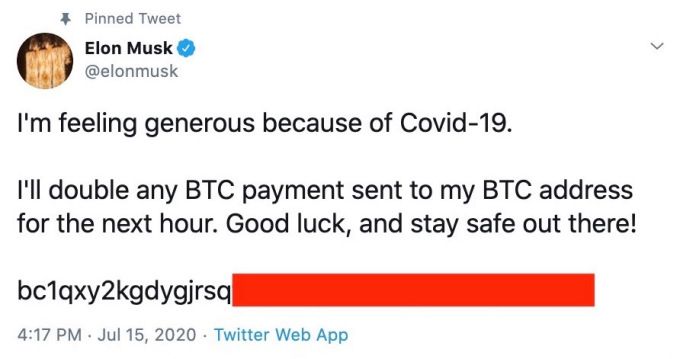
More plausibly, here’s Elon Musk:
Individual Twitter accounts get hacked all the time. But usually it’s a one-off event. Insecure passwords are one culprit, and two-factor authentication is another: hackers can execute a SIM-swap attack that lets them receive texts meant for your phone. Those texts can include login verification codes. But that doesn’t scale, and it certainly doesn’t happen all at once.
It’s unclear exactly how Twitter got hacked, but the two possibilities are:
- An inside job: a twitter employee either took over the accounts or gave someone else access to the tools necessary to do so. This has happened before. Two Twitter employees were charged with spying for Saudi Arabia, and one contractor, on his last day, temporarily deactivated Donald Trump’s account.
- Twitter’s internal account-level control panel got hacked. The best evidence for this is that Twitter has been suspending accounts that publish alleged screenshots of the tool. And some alleged hackers have taken credit for using this method. So far, this is where the evidence points.
Either way: someone had access to either every verified Twitter account or every Twitter account, period. And they used it to… scam a few people out of Bitcoin. The profits so far have been about $100,000.
I can easily think of several ways to make a quick billion dollars from having access to Twitter accounts, given lots of capital and a day or two of lead time:
- Russia or Saudi Arabia could announce an increase or decrease in oil production. Russia and Saudi Arabia could announce one.
- Donald Trump could resign, suspend the election, or announce that a pharma company with a liquid options market had produced a working vaccine that would be distributed to every American.
- Congress could extend unemployment benefits, or cancel them.
- Elon Musk could quit his job, or buy out a competitor. (Or take Tesla private again.) There’s precedent for this; Emulex dropped 60% after a fake press release, which worked especially well because it was released in the early morning East Coast time and Emulex employees rolled into the office late.
- The FTC could unwind the Instagram or YouTube deals.
- The Fed, ECB, or BOJ could do something interesting impacting the extraordinarily liquid FX market.
- Any head of state could threaten, or start, a war.
All of these are reasonable ways to prompt a massive swing in the value of a liquid market. The AP’s poorly-spellchecked hack tweet about a bomb attack on the White House pushed stocks down by about 1%, and had an impact on currencies and rates. A more coordinated effort—with a copyeditor involved—could have done more.
But the hackers didn’t do any of that. They did a Bitcoin scam instead. These scams have existed before: the classic method is to create an identical profile to a famous person (“EIon Musk,” for example), and reply to one of their tweets with a link to the scam. As hackers have gotten more sophisticated, they’ve gotten better at taking over verified accounts, changing their account details to the famous person’s, and running the same trick.
There are two explanations for the lame Bitcoin-scam payload for the hack. Both should make you less worried about cyber-security. One is that the hackers are dumb, and the other is that they’re actually quite smart.
If the hackers are dumb, they ran the Bitcoin scam because they didn’t know any better. Presumably these people had either been involved in, or knew about, the previous Bitcoin scams, and they pattern-matched “new Twitter security vulnerability” to “better harvest some more Bitcoin.” Someone who figures out how to infiltrate a major company is probably not stupid, but you wouldn’t necessarily expect them to be all that financially-literate.
But let’s assume our hackers made the same list of Twitter-driven market catalysts I did above. We could push the S&P, WTI, the 10-year, the Euro, the Yen, or any other large and liquid asset by 1% instantly, and we can move any stock price we want by up to 30% or so.
Okay, great. Now we have two problems: getting enough capital to make the trade, and realizing our profits. There’s a question of trust at one end, and law at the other. On the trust side, hackers have to convince someone with tens of millions of dollars that they can move the market. The best way to earn that trust is to actually move the market, but a big exploit only happens once. Within an hour or two of the first scam tweet, Twitter had locked all verified accounts from posting, and now seems to have tracked down (or at least mitigated) the original issue. So your criminals need to be very trustworthy. But also, they’re criminals. The whole thing sounds like its own scam: if you’re a hedge fund manager and an ostensible hacker says he can manipulate prices for your benefit, you should assume you’re not the co-conspirator, just the mark.[1]
But let’s imagine they do track down an investor who agrees to maximize profits from their trade in exchange for splitting those profits with them somehow. Where do these profits get realized? The SEC keeps an eye on accounts with suspiciously good timing. Especially if that timing involves a change in strategy. If a buy-and-hold equity investor makes their first-ever deep-out-of-the-money Eurodollar options trade and makes 50x their investment by predicting a headline, that will certainly get regulators' attention. You could act quickly, but an account that suddenly turns a huge profit and then liquidates and closes out will raise red flags. Brokers are risk-averse, and they’re not going to sacrifice much to protect a customer who is leaving anyway. So in any country that cooperates with the US regulatory regime, which is almost every country on earth, the partner-with-a-big-trader option is out.
But perhaps our hackers are smart enough to have thought of that, too. So they pick a jurisdiction where the SEC can’t come after them. Maybe China. Maybe Russia.
I can think of many misfortunes that might befall me in my life, but one of the worst would be:
- I have a billion dollars and have unknown but extensive control of Twitter, the main venue the President of the US uses to announce policy.
- I’m in Russia.
- Vladimir Putin is aware of both of these facts.
There just isn’t a great supply chain linking the ability to move markets through hacks to the ability to realize profits from those hacks. Both skills exist, independently, but the social gap, information gap, and trust gap make it almost impossible for the two to combine. Add that to the low probability of the hacks themselves—it’s not every day that someone exploits a major tech tech company so effectively—and the odds drop to nearly nil.
This is good news. The fact that cheesy Bitcoin scams work means that hackers have an incentive to break into vulnerable companies. But the fact that they work a lot better than more drastic exploits means that Bitcoin creates a sort of global bug bounty. If Bitcoin scammers hadn’t found this vulnerability, maybe North Korean hackers or the PLA would have.
If you’re a smart hacker who can break into Twitter and take over any account, bitcoin plus bragging rights may be the only payoff you have a reasonable chance to collect. If you want your Interactive Brokers account to briefly show a billion-dollar balance that you’ll never collect, you might as well edit your balance with Chrome’s DevTools. You’re just as likely to spend it that way.
[1] I suspect that in the wake of this hack, enterprising con artists will try to pull this off. I don’t know if we’ll hear about it; the victim should keep quiet, because getting away with it would be a serious crime. But I think it’ll happen.
Elsewhere
Jio!
Yesterday I mentioned that Google was considering a large investment in Reliance Jio. It’s official: Google is investing $4.5bn, making them the second-largest outside investor after Facebook ($5.7bn). There’s an idealistic case for investing in Jio, since it’s built a huge business and keeps launching new local-commerce products. And then there’s the cynical case, that it’s an investment in Reliance, which can wield a regulatory veto over competitors.
The Bans: Huawei Employees. Party Members? Dollars?
A common observation about markets in the last few years is that they’ve learned to ignore existential risk. The market tends to shrug off the possibility of things like nuclear war; it reacts a little, and recovers fast. One reason for this is that markets are relentlessly Bayesian. If there’s a surprising new development, it’s either random noise or it means we should expect many more such developments; bad news with no followup is noise, so rallies happen fast in the absence of tit-for-tat escalation.
So, what does it mean that, weeks after Hong Kong’s new security law went into effect, the US is restricting immigration from Huawei employees, and threatening to expel Chinese Communist Party members from the country and cut Chinese banks off from the dollar ($)? The latter two are extremely drastic: when party members send their kids to Harvard, it’s a symbol of the party’s power and a hedge against its collapse. And losing access to dollars would have a Covid-level impact on China (both in the sense that it would crush GDP in the short term and that the party would go to extraordinary lengths to normalize things in the longer term).
The election is in 109 days. Biden’s rhetoric against China is a hair less aggressive than Trump’s, and the status quo has strong anchoring effects: if Biden restored China’s early-2020 status quo, not to mention the pre-Trump status quo, this would read as a strongly pro-China move.
In other China/tech nationalism news:
- Yesterday, I mentioned the possibility that TikTok signed a long-term deal with Google Cloud Compute to free-ride on Google’s lobbying. Now TikTok itself is lobbying hard. Their parent company is also hedging, by focusing more on China ($). One notable fact about ByteDance is that they’ve launched, depending on how you count, two or three massively successful apps: Toutiao (news), Douyin (viral videos in China), and TikTok (viral videos everywhere else).
- Huawei remains hopeful that it will work with Canada. Canada, meanwhile, has been slow-walking a decision as their government waits to see whether China will release two Canadian nationals who have been imprisoned by the Chinese government.
Slacktivism at the New York Times
Slack is meant to be a communications tool, not a social network. But Slack channels, especially private channels, create a set of ad hoc social networks with real-time interactions and powerful filter bubbles. As a result, media companies have found that employees will organize on Slack and then pressure their employers on Twitter. Filter bubbles are not strictly bad—every new institution initially consists of the small set of people who ignore the outside world’s message that they’re working on something stupid. But the ability to cheaply form filter bubbles with push notifications is a novel threat. These internal filter bubbles reinforce the external ones: if the subset of New York Times employees who are upset about a decision the Times made can quickly find each other and coordinate a response, their ability to veto the Times‘ decisions is stronger, so its ideological range narrows. Google’s robust internal newsgroups had exactly the same effect, by helping employees who were upset about the same issue find each other and pick a message.
Whether this is a good thing or bad thing is a question for political philosophers. It makes companies more of a direct democracy than an administrative state. But tech companies can look at the city of San Francisco to see where direct democracy falls flat: it involves the promiscuous distribution of veto power to people with free time. A company with active Slack discussions will be more responsive to the will of their employees—but will be disproportionately responsive to the will of employees who spend all their time arguing on Slack instead of working.
Slackifying Gmail
Gmail is testing a redesign of Gmail that puts email, messaging, group chat, and video chat in the same app. If nothing else, this will complicate Slack’s messaging. Slack likes to say that their app replaces email, but both Google and Microsoft are now redesigning their email products around beating Slack.
Micro PE vs Value Capture
One bull thesis on Amazon’s ecommerce business is that third-party sellers are doing Amazon’s market research. For popular products, Amazon can launch their own white-label version; for less popular or more hit-driven ones, they’re happy to outside sellers shoulder the risk. Amazon swears up and down that they don’t access third-party sale data when launching their own products, but that’s not strictly true.
It may be true enough, though: Thrasio, a company that buys out successful Amazon retailers, has raised $260m. It doesn’t fully refute the thesis, though. Thrasio might be a nice example of applying financial theory in a practical way: first, it may be the case that the price at which Amazon sellers sell their business is determined by the perception that Amazon will copy them, while the actual risk is lower. Second, and more interesting: copying risk raises the variance of any given seller’s returns: if they don’t get copied, they do fine; if they do get copied, profits go away. So Thrasio might be structured around benefiting from the one free lunch in finance: if the market is efficient, switching from a concentrated portfolio to a diversified portfolio in the same asset class produces the same expected return, with less volatility.
Airbnb: Somewhat Back
Airbnb has announced one million bookings in a single day earlier this month. Bookings have shifted from international to local, and from long-term to short-term, so any room-nights-booked recovery in Airbnb will overstate the actual trend. Still, the direction is compelling, especially since some of their former supply is being converted back to long-term condo rentals.